
 Radio Frequency Identification (RFID) refers to a wireless system comprised of two components: Tags and Readers. An RFID tag is a chip attached to any object whose position is to be tracked. RFID tag consists of a unique code that identifies the object it is attached to. The reader is a device that has one or more antennas that emit radio waves and receive signals back from digital data encoded in RFID tags. RFID system consists of an antenna to communicate with scanning devices that can read the chip information remotely, a reader that emits a radio signal and receives information for tags, and a middleware that bridges RFID hardware with enterprise applications. Internet of Things (loT), refers to the collective network of connected devices and the technology that facilitates communication between devices and the cloud, as well as between the devices themselves. One of the main merits of loT and RFID integration in the supply chain is the ability to track goods in real time. RFID provides dependable connectivity between physical products and RFID readers that are connected to the internet. Most of these implementations take advantage of loT capabilities for sharing data between physical devices and cloud databases to support various authentication, transaction, analytics and control use cases.
Radio Frequency Identification (RFID) refers to a wireless system comprised of two components: Tags and Readers. An RFID tag is a chip attached to any object whose position is to be tracked. RFID tag consists of a unique code that identifies the object it is attached to. The reader is a device that has one or more antennas that emit radio waves and receive signals back from digital data encoded in RFID tags. RFID system consists of an antenna to communicate with scanning devices that can read the chip information remotely, a reader that emits a radio signal and receives information for tags, and a middleware that bridges RFID hardware with enterprise applications. Internet of Things (loT), refers to the collective network of connected devices and the technology that facilitates communication between devices and the cloud, as well as between the devices themselves. One of the main merits of loT and RFID integration in the supply chain is the ability to track goods in real time. RFID provides dependable connectivity between physical products and RFID readers that are connected to the internet. Most of these implementations take advantage of loT capabilities for sharing data between physical devices and cloud databases to support various authentication, transaction, analytics and control use cases.
Integrated Ultra High Frequency (UHF) RFID, and Internet of Things (loT) technologies, are exceptionally result oriented because of their wide range information-sharing capabilities throughout the supply chain to achieve real time tracking. Mobile Supply Chain Applications provide the ability to perform shop floor and warehouse transactions from any location in a facility using wireless radio frequency devices that can be hand-held, wearable, ring scanner systems, and lift truck mounted. Logistic mobile apps provide Real-time status of orders. 

Merits of loT and RFID integration -
Real time tracking ability of loT and RFID allows companies to have a much clearer picture of where goods are in the supply chain at any given time, and to take necessary steps as needed to ensure that goods are delivered on time. If a shipment is running behind schedule, the company can quickly identify the issue and take steps to resolve it, rather than waiting until the goods have already been delivered.
If a shipment of thermo-liable goods is being transported in a refrigerated truck, the company can use loT and RFID technologies to monitor the temperature of the goods to ensure that they are being kept at the proper temperature. This can help to reduce spoilage and waste, as well as improve the overall quality of the goods.
loT and RFID technologies can also be used to improve the efficiency of the supply chain by automating various processes. The developed supply chain systems by loT-RFID are used to automatically track manufacturing, update inventory levels as goods are received and shipped, eliminating the need for manual inventory management. Similarly, loT sensors can be used to automatically trigger actions, such as reordering supplies or routing goods to a different location, based on real-time data. These technologies are helping companies to reduce costs, improve the quality of goods, and deliver goods more efficiently to their customers.
such as reordering supplies or routing goods to a different location, based on real-time data. These technologies are helping companies to reduce costs, improve the quality of goods, and deliver goods more efficiently to their customers.
Factors that have contributed to the growing popularity of loT and RFID technologies in the supply chain companies are as under –
- Declining costs of loT and RFID technologies,
- Improved technology reliable and easier to use,
- Consumers demanding efficiency, real-time data on the location and condition of goods more transparency and visibility in the supply chain which can help logistics and supply chain companies to better understand and manage their operations.,
- The rise of e-commerce business,
- Reduced errors in the supply chain, such as incorrect shipments, missed deliveries and lost or damaged goods.
- Improved customer satisfaction:
- Sustainability efforts through optimization routes and reduce waste.
- Increased competitiveness to offer more efficient and reliable service to their customers.
- Emergence of paperless shipping documentation FAST tag implementation
- SG leads to more RFID adoption
RAIN RFID SOLUTIONS
The term RAIN is derived from Radio Frequency Identification, also known as RFID. But it is a cloud based infrastructure where RFID data can be stored, managed, and shared via the Internet. There are frequency ranges that RFID technology uses are – Active UHF (433 MHz) range of up to 100 meters and Passive UHF (860-960 Mhz). RFIDs that are RAIN certified are called RAIN RFID. RAIN is an authority that certifies certain Passive UHF RFID based on their qualities. RAIN is the brand name for Passive Ultra High Frequency (UHF) RFID technology. The RAIN Communication Interface (RCI) guideline allows RFID tag manufacturing companies to offer tags that could operate with any reader, thereby enabling deployments with multiple reader types and offering a solution that could be used at multiple customer sites. For example, integrating a RAIN RFID solution allows items to be automatically read as they pass through transition points, replacing the time-intensive and reparative task of manually scanning items one by one. RAIN RFID is used in many applications, including inventory management, asset tracking, and shipment verification. RAIN is the fastest growing segment of the RFID market and uses a single global standard: UHF Gen 2 (ISO/IEC 18000-63).
RAIN RFID solutions include three elements –
- Endpoints – Endpoints are products and their RAIN RFID tag chips that uniquely identify the product.
- Connectivity – A smart edge devices that enable wireless, bi-directional communication with endpoints.
- Software – The software arranges and transforms data from endpoint reads, delivering real-time information to enterprise and consumer applications.
RAIN tag is made from an integrated circuit (tag chip) and an antenna mounted on a substrate. Different companies offer variety of features in these tags like security, file management features, user memory, and the ability to add “battery assist:’These chips use wireless communication which means that they do not require ‘line- of- sight.’They have a capacity to scan up to 1,000 units/second. Many readers can also write on the tag.
There are two types of readers: fixed and portable(hand-held), and they come in many variations. Fixed readers are mounted to a fixed location and can communicate with one-to-many antennas. Readers usually require a power supply and are connected to a network with an Ethernet cable. Portable readers can be as small as to be configured in the mobile phones.
TRACK AND TRACE SOLUTION
Track and Trace solutions deals with the process of determining the current and past locations of a product. This solution comes with both Barcode as well as Radio Frequency Identification (RFID). Barcode technology is a common and cost-effective method. RFID is more effective than Barcode but at the same time, there is a cost involved to implement RFID. However, RFID is adopted in supply chains.
 The worldwide track and trace arrangements advertise is required to witness significant development during the figure time frame because of components, for example, increment in a selection of track and trace arrangements by medicinal gadget and pharmaceutical makers to conquer the issue of medication fake and organized administrative system and execution of measures. Even though these components earn the development of the market, high establishment cost related to serialization and total arrangements significantly ruin the market development.
The worldwide track and trace arrangements advertise is required to witness significant development during the figure time frame because of components, for example, increment in a selection of track and trace arrangements by medicinal gadget and pharmaceutical makers to conquer the issue of medication fake and organized administrative system and execution of measures. Even though these components earn the development of the market, high establishment cost related to serialization and total arrangements significantly ruin the market development.
The Track and Trace arrangements advertise is fragmented dependent on item type, innovation, application, end client, and topography. Given an item, the market is bifurcated into equipment frameworks and programming arrangements. The equipment frameworks advertise is further classified into printing and stamping arrangements, checking and verification arrangements, marking arrangements, and others. The product arrangements showcase is sub-divided into plant chief programming, line controller programming, a group following programming, and others. Because of innovation, track, and trace arrangements advertise is divided into standardized identification and RFID.
loT-RFID technology can resolve anti-counterfeiting problems faced by supply chain. Incorporate design elements into packaging to make counterfeiting more difficult. Holographs and other detection elements can add layers of security to these already established technologies.
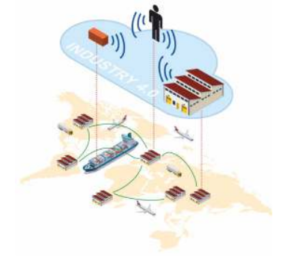
SMART SUPPLY CHAIN 4.0
Supply Chain 4.0 refers to reorganising supply chains from design, planning, manufacturing, distribution, consumption, and reverse logistics – using “Industry 4.0″technologies.Technologies such as the application of the Internet ofThings (loT), advanced robotics, and advanced analytics of big data to manage supply chains. Better visibility into data and analytics leads to smarter, quicker, and more efficient decisions. By improving basic metrics and reporting, organisations can access data that will increase performance and offer visibility into all supply chain activities. Using sensors in everything, creating networks everywhere, and automation and analyzation of everything, can significantly improve performance and customer satisfaction. With Artificial Intelligence, supply chain managers can accurately determine optimal stock levels, identify slow-moving items, and predict potential stockouts or overstock situations. Such insights enable businesses to streamline inventory management, improve order fulfillment, and reduce holding costs. Blockchain is a method of recording information that makes it impossible or difficult for the system to be changed, hacked, or manipulated.
 Supply Chain 4.0 will make organization faster, more flexible, more granular, more accurate, and more efficient. Supply chain organisations are in the phase of digital transformation to the next-generation digital supply chain. Next-generation asset tracking solutions based on Bluetooth Low Energy (BLE) and Ultra wideband (UWB) will rapidly replace expensive legacy systems such as passive Radio Frequency Identification (RFID) while providing increased location granularity.
Supply Chain 4.0 will make organization faster, more flexible, more granular, more accurate, and more efficient. Supply chain organisations are in the phase of digital transformation to the next-generation digital supply chain. Next-generation asset tracking solutions based on Bluetooth Low Energy (BLE) and Ultra wideband (UWB) will rapidly replace expensive legacy systems such as passive Radio Frequency Identification (RFID) while providing increased location granularity.
Smart supply chains can foster innovation and creativity in the Industry 4.0 environment by providing businesses with the tools, data, and opportunities to explore new possibilities and solutions, collaborate and co-create, and learn and adapt. By collecting and analyzing data from various sources, businesses can reveal new insights, trends, and patterns that can inspire new ideas and solutions. Smart supply chains also enable businesses to test and validate their ideas and solutions faster and cheaper, by using technologies such as simulation, digital twins, and rapid prototyping. Additionally, businesses can enhance their collaboration and communication with their internal and external stakeholders, such as their employees, partners, suppliers, and customers. Smart supply chains allow businesses to share and exchange data, information, and feedback, and to co-create value and innovation. Furthermore, businesses can monitor and measure their performance and impact and identify and address the gaps and opportunities for improvement and innovation. Smart supply chains also enable businesses to be more agile and resilient, by allowing them to adjust and optimize their supply chain operations and processes in response to the external and internal factors.
![]() A blockchain is a distributed, digital ledger. The ledger records transactions as a series of blocks that are linked together sequentially in a chain. The key quality of the blockchain is the transparent and immutable record of all transactions within the supply chain. This facilitates the tracing of products from their origin to their destination, improves accountability and reduces the risk of fraud. This also provides greater transparency within the supply chain and allows companies to track products and monitor performance in real time. This in turn can also improve trust between partners within the supply chain.
A blockchain is a distributed, digital ledger. The ledger records transactions as a series of blocks that are linked together sequentially in a chain. The key quality of the blockchain is the transparent and immutable record of all transactions within the supply chain. This facilitates the tracing of products from their origin to their destination, improves accountability and reduces the risk of fraud. This also provides greater transparency within the supply chain and allows companies to track products and monitor performance in real time. This in turn can also improve trust between partners within the supply chain.
Challenges of smart supply chain system Smart supply chains challenges include-
• Cybersecurity and data privacy,
• Integration and interoperability,
• Change management and culture,
• Data quality and integration
• Technology adoption and interoperability
• Organizational culture and alignment
• Regulatory compliance and ethical responsibility
• Innovation and differentiation
To overcome these challenges and optimize Supply Chain Management (SCM) processes, organizations can turn to Artificial Intelligence (AI) and Machine Learning (ML) technologies.
The integration of Artificial Intelligence and Machine Learning into SCM has the potential to revolutionize the industry. From demand planning to production scheduling and delivery optimization, AI and ML technologies offer new possibilities for streamlining processes, increasing efficiency, and improving customer satisfaction. By leveraging advanced modeling techniques, segmentation algorithms, reinforcement learning, and autocorrection capabilities, organizations can enhance their supply chain operations and achieve better outcomes. The use of digital twins, AI-based chatbots for the Core SCM Team, anomaly detection algorithms, and AI/ML- based delivery optimization further adds to the potential benefits of incorporating AI and ML in SCM. Since AI and ML continue to advance, SCM vendors are likely to incorporate these technologies into their solutions, making supply chains more intelligent, automated, and self-healing. Organizations that embrace AI and ML in their SCM processes will gain a competitive edge in today’s rapidly evolving business landscape.
Cybersecurity Risks Mitigation in Supply Chain
A supply chain cybersecurity risk is a type of cyberattack carried out against an organization’s suppliers to gain unauthorized access to that organization’s systems or data or stolen data breaches/data loss. Cybersecurity risk arises due to compromised software or hardware purchased from disputed suppliers, Software security vulnerabilities in supply chain management or supplier systems, and Counterfeit hardware or hardware with embedded malware. Threats to cybersecurity are phishing and social engineering, Ransomware and Malware, weak Passwords, poor patch management, insider threats, etc. The three main Risk Assessment stages are Identify, Assess, and Manage.
Addressing the cyber security risks in supply chains may be complex, but organisations that take a systematic and collaborative approach will find themselves well-placed to mitigate threats, adapt quickly to changes in the business environment, and respond swiftly if an incident occurs. Assessing the criticality of the organisation’s information systems and assets will help to understand which of these require the most resources allocated to their protection against supply chain threats. Identifying which suppliers provide the most vital assets and services will illuminate the areas of the supply chain that demand the most attention. Evaluating the security posture of prospective suppliers during the procurement phase should provide vital information to support decisions. Security requirements and ongoing expectations should be agreed in writing. Maintaining open, collaborative relationships with suppliers will help to ensure security information flows both ways. the organization can be placed in a strong position to mitigate risks and direct cyber security resources into the most vital areas by actively monitoring the cyber threat landscape, evaluating threats against own systems, assets, and processes, and adjusting controls as necessary.
 Establishing a programme for managing supply chain cyber security risk and gaining buy-in from senior management staff and board members will formalise and embed the process in a structured way. The programme should be integrated into the organisation’s wider risk assessment procedures, with all affected areas involved in the risk management process. Recognise that human factors, rather than technology alone, can often be the enablers of cyber incidents. Provide high quality training and guidance to organisation staff, especially those in key positions, and reinforce a positive culture of cyber security awareness. Ensure that organisational risk tolerances are well-defined and accessible.
Establishing a programme for managing supply chain cyber security risk and gaining buy-in from senior management staff and board members will formalise and embed the process in a structured way. The programme should be integrated into the organisation’s wider risk assessment procedures, with all affected areas involved in the risk management process. Recognise that human factors, rather than technology alone, can often be the enablers of cyber incidents. Provide high quality training and guidance to organisation staff, especially those in key positions, and reinforce a positive culture of cyber security awareness. Ensure that organisational risk tolerances are well-defined and accessible.
 Businesses must invest in robust and reliable security measures and policies to protect their data and systems from unauthorized access and misuse. They must ensure that their systems and processes are compatible and interoperable and that they can integrate and communicate with each other. They must have the skills and capabilities to leverage smart supply chain technologies and processes. They must manage the change and transformation effectively.
Businesses must invest in robust and reliable security measures and policies to protect their data and systems from unauthorized access and misuse. They must ensure that their systems and processes are compatible and interoperable and that they can integrate and communicate with each other. They must have the skills and capabilities to leverage smart supply chain technologies and processes. They must manage the change and transformation effectively.
References:
- Knut Alicke and Jurgen Rachar, McKinsey & Company Article, October 27, 2016.
- Advanced Mobile Group Article, Decision point Company, Nov 25, 2022.Material Handling & Logistics Article, January 10, 2018.
- Weng Chun Tan and Manjit Singh Sidhu, Elsevier, 2022, Volume 9, Issue C.
- Steve Wilson, Capgemini Consulting Article, May 18, 2020.
- Weng Chun Tan, Manjit Singh Sidhu, Sharulhizam Mohamad Shah, Turkish Journal of Computer and Mathematics EducationVol.12 No.3 (2021), 1754-1762.
- Alan R. Earls, Supply Chain and Manufacturing Article, 31 Oct 2022.
- Marcin, Applandeo Article, Dec 29th 2022. Supply Chain Management, Linkedin.
- Article by National Cyber Security Centre, New Zealand.

Exclusives
by Gerardo Gomez
Director QMC-USA and CQV SME, PharmaLex
An article for Digital transformation is the process of using digital technologies to create new or modify existing business processes – By Satish Desai






